How to Use and Install Gremlin on Amazon Linux
Introduction
This tutorial will walk through how to install Gremlin on Amazon Linux and perform a Chaos Engineering experiment using a Gremlin CPU attack.
Prerequisites
Before you begin this tutorial, you'll need the following:
- An AWS account (sign up here)
- A Gremlin account (request a free trial)
Step 1 - Spin up an instance running Amazon Linux
First open AWS console, click to launch an instance and select Amazon Linux 2 as your AMI. When your instance starts click on “Connect” to identify how to connect via SSH to your new instance.
Your connection string will look similar to the following, paste this string into terminal and connect to your instance:
Step 2 - Installing iproute-tc
When using Amazon Linux 2 you will first need to install iproute-tc, Amazon Linux 1 comes pre-installed with iproute-tc:
Step 3 - Installing the Gremlin Daemon and CLI
Next, add the Gremlin repository:
Then install the Gremlin daemon and CLI:
After you have created your Gremlin account you will need to find your Gremlin Daemon credentials. Login to the Gremlin App using your Company name and sign-on credentials. These were emailed to you when you signed up to start using Gremlin.
Navigate to Team Settings and click on your Team. Make a note of your Gremlin Secret and Gremlin Team ID.
Then initialize Gremlin and follow the prompts:
You are now ready to create attacks using the Gremlin App.
Step 4 - Creating attacks using the Gremlin App
Example: The Hello World of Chaos Engineering (a CPU attack)
You can use the Gremlin App, Gremlin CLI or the Gremlin API to trigger Gremlin attacks.
Using your Gremlin login credentials (which were emailed to you when you created your account), log in to the Gremlin App. Then click Create Attack.
First, choose your target by selecting the host you registered with Gremlin. Next, we will use the Gremlin App to create a CPU Attack. Choose the Resource Category and Select the CPU Attack. Click Unleash Gremlin and the Gremlin CPU Attack will consume CPU resources on your host.
You can now view the Gremlin CPU Attack in Datadog:
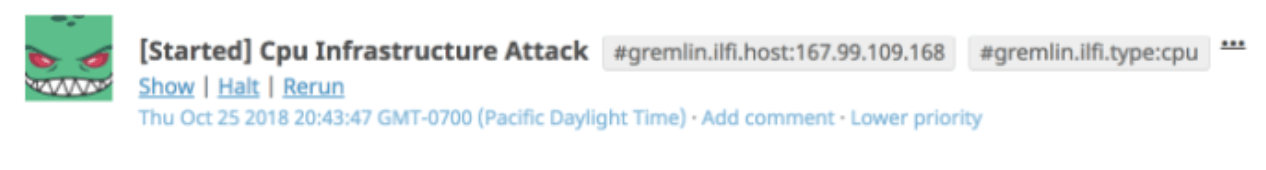
Your attack will begin to run, you will be able to view its progress via Gremlin Attacks in the Gremlin App.
On your server, run top to check the impact of the Gremlin Attack. When your attack is complete it will move to Completed Attacks.
Step 5 - Halting a CPU resource attack using the Gremlin App
You can stop a Gremlin Attack at anytime using the Gremlin App. Simply click on the halt button for a specific attack or click Halt All Attacks.
Conclusion
You've installed Gremlin on an instance running Amazon Linux 2 and validated that Gremlin works by running the Hello World of Chaos Engineering, the CPU Resource attack. Next, we recommend running different types of Gremlin Attacks, including attacks that impact State and Network.
Share your results and swap best practices with 5,000+ engineers practicing Chaos Engineering in the Chaos Engineering Slack.
Join the Chaos Engineering Slack
Connect with 5,000+ engineers who are building more reliable systems with Chaos Engineering.
Avoid downtime. Use Gremlin to turn failure into resilience.
Gremlin empowers you to proactively root out failure before it causes downtime. See how you can harness chaos to build resilient systems by requesting a demo of Gremlin.

.svg)

.svg)
.svg)

 This is an older tutorial
This is an older tutorial