Automating a Chaos Engineering Environment on AWS with Terraform
Chaos as Code (CaC) enables you to simply, safely and securely run, schedule and manage Chaos Engineering experiments. This tutorial will demonstrate how to use Hashicorp Terraform to automate your Chaos Engineering experiments.
Hashicorp’s Terraform is an open source tool that enables you to define infrastructure as code, increasing productivity and transparency. Terraform codifies APIs into declarative configuration files that can be shared amongst team members, treated as code, edited, reviewed, and versioned.
In this tutorial, we will demonstrate how to use Terraform to create an EC2 instance and setup Gremlin to perform Chaos Engineering experiments. You will then perform a Chaos Engineering experiment on your EC2 instance in the form of a Gremlin Latency Attack. This tutorial will help you get started with using Terraform, and give you an idea of how it can be used for Chaos as Code (CaC).
Prerequisites
- AWS Account (see EC2 permissions in Appendix A)
- Gremlin Account (with Team ID and Secret ready - sign up here)
- Terraform (for automating resource creation)
- AWS CLI (nice to have to interact with your AWS environment)
Step 0: Verify Terraform Installation
If you don’t have Terraform installed, You can download the appropriate package here.On your local machine, verify your Terraform installation. You should see output like this:
Step 1: Create the VPC Environment
For separation, create two directories, one for VPC specification and another for Instance specification.
On your local machine:
Inside the vpc directory, create the following <span class="code-class-custom">vpc.tf</span> file using a text editor. We'll use vim throughout this tutorial. Replace the example region/az, tags, IP space and security group as required to set these up correctly for your AWS VPC.
Enter the following information, changing the <span class="code-class-custom">region</span>, <span class="code-class-custom">name</span>, <span class="code-class-custom">cidr</span>, <span class="code-class-custom">azs</span>, <span class="code-class-custom">public_subnets</span>, <span class="code-class-custom">owner</span>, <span class="code-class-custom">environment</span>, <span class="code-class-custom">name</span>, and <span class="code-class-custom">description</span> fields with your own data.
This <span class="code-class-custom">vpc.tf</span> terraform template file uses the aws provider, defines a VPC with a single public subnet in an availability zone, and a security group within this VPC to allow SSH access.
Let’s run a couple of commands to stand up the underlying networking infrastructure.
On your local machine:
Terraform will compute the resources that needs to be created, and you will then be prompted:
Enter <span class="code-class-custom">yes</span>, and Terraform will go ahead and create the resources. On successful completion you will see the following result:
Note the Security Group ID (sg-xxxxxxxx) and Subnet ID (subnet-xxxxxxxx) for later.
That’s it! With just a few commands you have created a new VPC with internet gateway, a subnet in <span class="code-class-custom">us-west-2a</span>, a route table for the public subnet, and a security group allowing ssh access.
Step 2: Launch an Instance that registers to Gremlin
Now that you have the underlying networking environment prepared, and let’s focus on automating the creation of an instance.
Switch to the instance directory you created in Step 1:
Create the <span class="code-class-custom">instance.tf</span> template that defines the specification of the instance to launch. It references the <span class="code-class-custom">userdata.sh</span> script to install and authenticate a Gremlin agent at launch. You will create this <span class="code-class-custom">userdata.sh</span> file at a later step.
To populate the <span class="code-class-custom">instance.tf</span> template, you will need the following
- EC2 SSH key name
- Security Group ID
- Subnet ID
If you do not recall the Security Group ID and/or the Subnet ID from the earlier step, you can retrieve them via the aws cli.
This is an example of the result you will see:
This is an example of the result you will see: <span class="code-class-custom">subnet-cbbd68b2</span>
Populate <span class="code-class-custom">instance.tf</span> template file with the following content. Modify <span class="code-class-custom">your_name</span>,<span class="code-class-custom"> subnet_id</span>, <span class="code-class-custom">vpc_security_group_ids</span>, and <span class="code-class-custom">key_name</span> accordingly.
On your local machine in the /terraform/instance directory, create the <span class="code-class-custom">instance.tf</span> file:
Note: If you are new to vim or need a refresher for vim commands, refer to this vim cheatsheet.Enter the following information, modifying <span class="code-class-custom">region</span>, <span class="code-class-custom">name</span>, <span class="code-class-custom">subnet_id</span>, <span class="code-class-custom">key_name</span>, and <span class="code-class-custom">Owner</span> accordingly:
This instance template file defines a t2.micro EC2 instance from the latest Amazon Linux AMI, to be launched in the specified subnet, with the SSH security group created earlier.
Downloading your Gremlin agent certificates
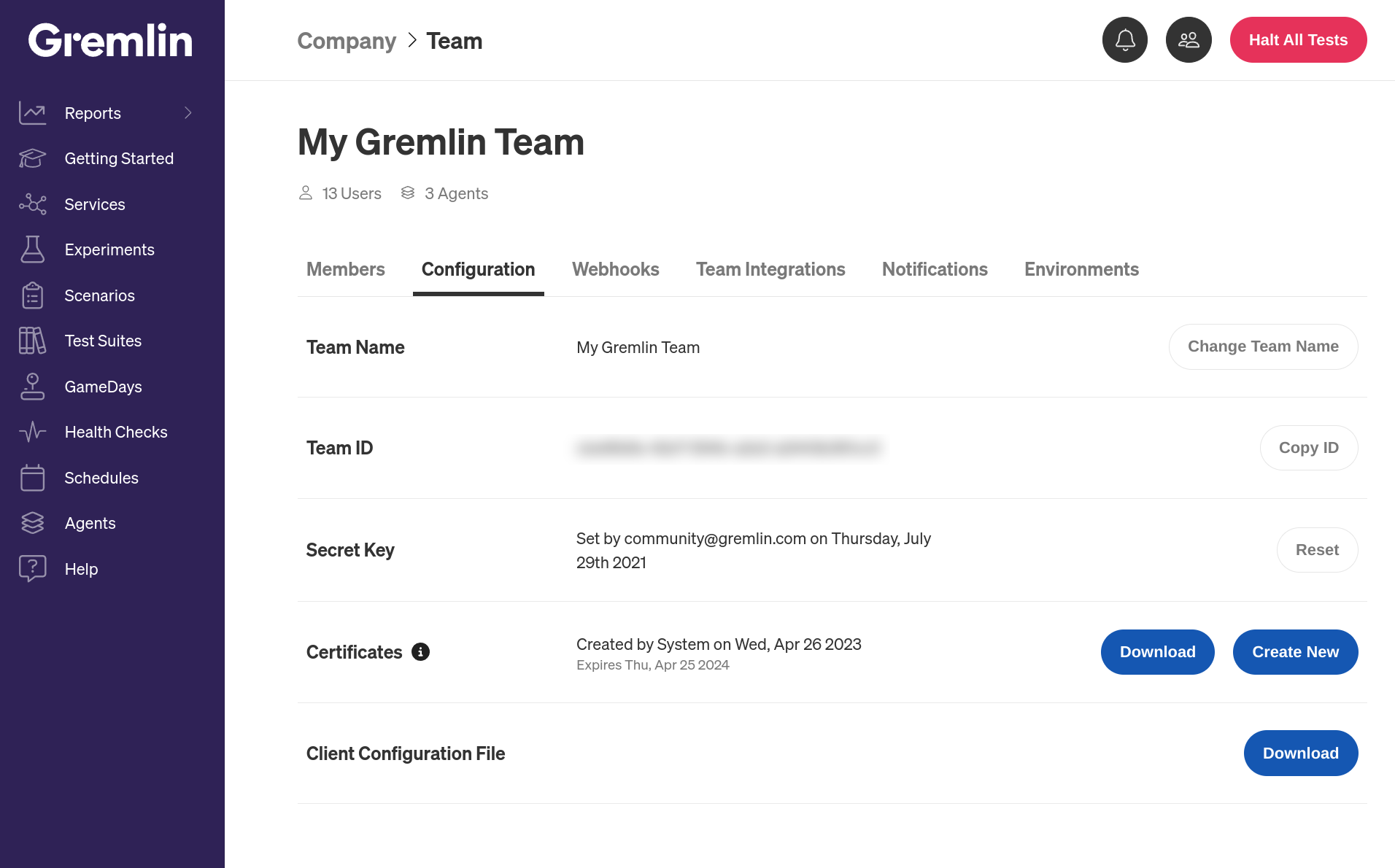
After you have created your Gremlin account (sign up here) you will need to find your Gremlin agent credentials. Login to the Gremlin App using your Company name and sign-on credentials. These were emailed to you when you signed up to start using Gremlin.
Next, navigate to the Team Settings page by clicking the user icon in the top-right corner of the screen (next to the Halt button) and selecting Team Settings. Click on the Configuration tab, then click the blue Download button to save your certificates to your local computer. The downloaded certificate.zip contains both a public-key certificate and a matching private key.
Unzip the downloaded certificate.zip on your laptop. Next, we will create the <span class="code-class-custom">userdata.sh</span> script.
On your local machine in the /terraform/instance directory, create the <span class="code-class-custom">userdata.sh</span> file:
Enter the following information, replacing <span class="code-class-custom">GREMLIN_TEAM_ID</span> with your Gremlin team ID, <span class="code-class-custom">GREMLIN_CERTIFICATE</span> with the contents of your public certificate (your <span class="code-class-custom">pub_cert.pem</span> file), <span class="code-class-custom">GREMLIN_PRIVATE_KEY</span> with the contents of your private key (your <span class="code-class-custom">priv_key.pem</span> file), and <span class="code-class-custom">YOUR_NAME</span> with your name:
This script adds the gremlin repository, installs the Gremlin agent and daemon, sets the configuration file with authentication details and instance tags, and finally starts the service to connect as a agent to Gremlin.
With everything ready, let’s run these templates.
Again, indicate yes and Terraform will bring up an EC2 instance.A successful result will appear as below:
Now turn to the Agents page on Gremlin Control Panel.
You should see your newly brought up instance as an Online agent on Gremlin. Hooray!
Step 3: Run Your First Attack in your own Chaos Environment
Prepare a new Latency Gremlin Attack targeting the newly registered instance, but do not execute the attack just yet.
- Log into the Gremlin web app.
- Click Attacks in the left navigation bar, then click New Attack.
- Select the Infrastructure tab, then select your EC2 instance. An easy way to find your instance is by entering its IP address or hostname in the search box.
- Scroll down and click on the Choose a Gremlin section. Select the Network category, then select Latency.
Before starting the attack, SSH into the instance using your key file and start pinging www.google.com. You can do this by running the following commands on your local machine (make sure to swap in your own key file and IP address in place of <span class="code-class-custom">mykey.pem</span> and <span class="code-class-custom">34.214.21.96</span>.
Switch back to the browser where you have the Gremlin web app open and click Unleash Gremlin to execute the latency attack. Once the attack enters the <span class="code-class-custom">Running</span> stage, switch back to the terminal where ping is running. You should see the round trip time increase by 100ms similar to the output below (note the change between lines 3 and 4):
Congratulations! In a very short amount of time, you have automated the creation of a completely new environment apart from the rest of your running resources, launched an instance that connects automatically to Gremlin, and ran your first attack in this environment.
If you are feeling adventurous, we highly recommend that you play around with Terraform. Create additional subnets in more availability zones. Create private subnets that talks through NAT gateway to the internet. Increase the instance count to launch more Gremlin instances. Also take a stab at running other attacks with Gremlin in this environment.
Step 4: Cleaning up.
Let’s first terminate the instance.
On your local machine:
Similar to the creation of resources, Terraform will need you to confirm if you really want to destroy the resources.
Enter yes, and Terraform will go ahead and destroy the resources.
Now go ahead and also destroy the VPC.
On your local machine:
Next time you want to spin up the environment again, simply use the templates you have used here, and you have your chaos environment within minutes.
Conclusion
By templatizing your chaos environment, you are able to quickly spin up an environment, run an attack to purposefully inject fault into the system, and return to zero footprint when you are done. Expanding on what you have achieved, if you also bring up your application within this environment, you're also able to evaluate and validate its resiliency against specific real-life operational scenarios. With the basics of running attacks down, you may want to think about running GameDays. If you need some help, here is How to Run a GameDay.
Appendix A - EC2 Permissions
You should have no issues if your user have the AdministratorAccess or AmazonEC2FullAccess policy attached. Otherwise, you will need permissions to the following API:
Avoid downtime. Use Gremlin to turn failure into resilience.
Gremlin empowers you to proactively root out failure before it causes downtime. See how you can harness chaos to build resilient systems by requesting a demo of Gremlin.

.svg)

.svg)
.svg)

 This is an older tutorial
This is an older tutorial